Blog > Consulting > Authentication with Tibco Spotfire®
Written on April 18, 2023
Authentication has become a major challenge for data management, whether to secure access to sensitive information or to ensure a level of reliability in its use. With Tibco Spotfire®, this problem is even more important as this solution allows to carry out in-depth analysis using data from multiple sources.
Tibco Spotfire® offers several authentication options, such as internal authentication, OpenID and LDAP. However, in some cases, these standard options do not correspond to the specific needs of a company or a project. Thus, Tibco Spotfire® offers a personalised authentication solution: the Custom Authenticator. This solution makes it possible to adapt authentication according to the specific needs of a company or organisation and to set up stricter security rules.
"Authentication is a crucial issue for data management and analysis. The dataLearning teams are specialised in the deployment of Tibco Spotfire®, Web Player, Automation services."
Pierre Ibarra
CustomAuthenticator
A CustomAuthenticator is a custom authentication mechanism that allows custom authentication workflows to be created for Tibco Spotfire®. It allows customisation of authentication processes based on specific business needs, such as integration with third-party systems, specific security requirements, or complex authentication workflows.
CustomAuthenticators are based on the Tibco Spotfire® Authentication Framework, which provides a standard interface for user authentication. This interface allows CustomAuthenticators to seamlessly integrate with the standard Tibco Spotfire® user interface, including the login page and user management. CustomAuthenticators can be developed using different programming languages, such as Java, .NET, Python, or even R code. They can also be hosted on a variety of platforms, including Java application servers and cloud services such as AWS Lambda.
You will find more information directly on the Tibco website by following the following link.
Tibco Spotfire® embeds libraries through its CustomAuthenticators that allow the use of JSON Web Tokens (JWT) for authentication. This technology helps validate, and verify a user’s authentication and provides authorisation features to determine what actions can be performed with the data.
"A CustomAuthenticator is a custom authentication mechanism that allows custom authentication workflows to be created for Tibco Spotfire®."
Pierre Ibarra
Json Web Token (JWT)
A JWT is a simple and secure way to transfer information between multiple parties, especially for user authentication and authorisation in web applications.
A JWT is a JSON object that contains user information, signed by the application server. The JWT is then passed to the client and included in every WEB request to authenticate the user to other resource providers. JWTs are used as an alternative to session cookies or OAuth access tokens.
A JWT consists of three parts separated by dots:
Header: contains the token type (typ) and the signature algorithm (alg)
Payload: Contains user information, permissions, and token metadata.
Signature: verifies the integrity of the token and guarantees that the information it contains has not been altered.
The main interest of JWT lies in its portability and security. It can be issued by a server to authenticate a user and then transmitted to another server to access a protected resource.
"A 'JSON Web Token' (JWT) is an easy and secure way to transfer information between multiple parties, especially for user authentication and authorisation in web applications."
Pierre Ibarra
Implementation
Tibco Spotfire® embeds Nimbus/Jose Java libraries for JWT token management. These provide a large number of examples with different encryption algorithms such as HMAC, RSA, EC or EdDSA.
In our case, we are using EC384. JWT offers the possibility of encrypting the entire Header/Payload/Signature trio, but we will only see the signature verification part here.
Here is the example provided by Connect2id in our case:
import java.util.Date;
import com.nimbusds.jose.*;
import com.nimbusds.jose.crypto.*;
import com.nimbusds.jose.jwk.*;
import com.nimbusds.jose.jwk.gen.*;
import com.nimbusds.jwt.*;
// Generate an EC key pair ECKey ecJWK = new ECKeyGenerator(Curve.P_384)
keyID("123")
generate();
ECKey ecPublicJWK = ecJWK.toPublicJWK();
// Create the EC signer
JWSSigner signer = new ECDSASigner(ecJWK);
// Prepare JWT with claims set
JWTClaimsSet claimsSet = new JWTClaimsSet.Builder()
subject("alice")
issuer("https://c2id.com")
expirationTime(new Date(new Date().getTime() + 60 * 1000))
build();
SignedJWT signedJWT = new SignedJWT(
new JWSHeader.Builder(JWSAlgorithm.ES384).keyID(ecJWK.getKeyID()).build(),
claimsSet);
// Compute the EC signature
signedJWT.sign(signer);
// Serialize the JWS to compact form
String s = signedJWT.serialize();
// On the consumer side, parse the JWS and verify its EC signature
signedJWT = SignedJWT.parse(s);
JWSVerifier verifier = new ECDSAVerifier(ecPublicJWK);
assertTrue(signedJWT.verify(verifier));
// Retrieve / verify the JWT claims according to the app requirements
assertEquals("alice", signedJWT.getJWTClaimsSet().getSubject());
assertEquals("https://c2id.com", signedJWT.getJWTClaimsSet().getIssuer());
assertTrue(new Date().before(signedJWT.getJWTClaimsSet().getExpirationTime()));Note that the environment used for our example is a Linux server and that the compilation and configuration of Spotfire may vary on a Windows server.
On the Spotfire side, it may be necessary to add libraries for the specific processing induced by the use of JWT tokens. They must be added to the tomcat/lib directory before restarting Spotfire for them to be taken into account.
Adding “specific” code is done by adding “custom-ext” in Tibco Spotfire®. These modules will be automatically loaded when the server starts.
Once our code is prepared in the lab, the integration will be done as follows:
... /tomcat/custom-ext/com/tibco/spotfireps/server/security/CustomAuthenticator.java2- Once our code is implemented, we compile using Spotfire-specific resources:
…/jdk/bin/javac -classpath "…/tomcat/webapps/spotfire/WEB-INF/lib/*:…/tomcat/spotfire-boot-lib/*:…/tomcat/lib/*" -d . …/tomcat/custom-ext/com/tibco/spotfireps/server/security/CustomAuthenticator.java3- We then create our package which will be loaded when Spotfire starts if custom authentication is enabled:
jar -cvf CustomAuthenticator.jar4 – Finally, we activate our custom code:
sudo -u spotfireuser ./config.sh config-external-auth -e true --custom-authenticator-class-name=com.tibco.spotfireps.server.security.CustomAuthenticator
sudo -u spotfireuser ./config.sh import-config --comment="ActivationCustomAuth"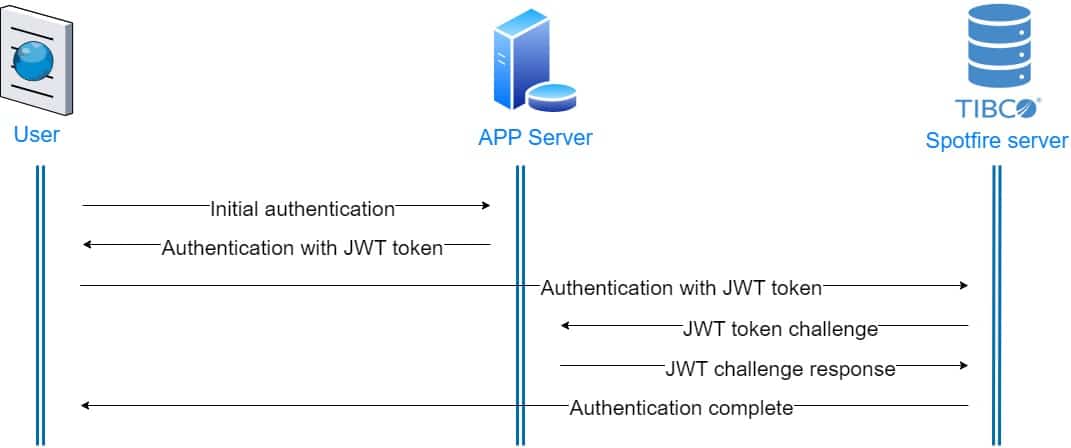
Conclusion
Authentication is a crucial issue for data management and analysis. The dataLearning teams are specialised in the deployment of Tibco Spotfire®, Web Player, Automation services but can also help you with specific developments, as well as training your teams in data visualization with Tibco Spotfire®.
By reaching out to the dataLearning teams, Tibco Spotfire® customers can be assured they will get a personalised and effective authentication solution, while benefiting from technical expertise adapted to their level of knowledge.
Finally, we invite you to read our other article on “Spotfire: or how to give meaning to your data”.
